Key Takeaways
- Two-factor authentication (2FA) is essential for safeguarding on-line accounts and requires fixing two identification exams with data solely you’ll know.
- {Hardware} safety keys present a bodily dongle that replaces the second issue of authentication in your cellphone, providing enhanced safety towards safety breaches.
- Numerous producers produce {hardware} safety keys that work with standard net browsers, apps, and on-line companies, making them simple to make use of and comparatively cheap for added account safety.
When you’ve got an account on-line someplace that is solely being protected by a password, irrespective of how good it’s, it simply is not sufficient nowadays. That makes the way you deal with two-factor authentication extra vital than ever.
Nonetheless, in case you really feel a private safety breach may need an outsized affect on not simply your life, however the lives of your loved ones, buddies, or firm, you may want to contemplate getting a {hardware} safety key in case you do not have already got one. We clarify what a {hardware} secret is and what your choices available on the market are.
What precisely is two-factor authentication (2FA)?
Two-factor authentication – also called 2FA – means it’s good to remedy two identification exams with data solely you would know to achieve entry to an account.
For the primary component, practically each platform defaults to the usual password, however a few of them are beginning to assist passkeys. For those who’re not present on what a passkey is, we have an explainer for that.
The second component must be trickier; thus, the strategies can fluctuate broadly. Google presents an entire bunch of second-factor strategies that confirm you are holding a cellphone that is already logged into your Google account whereas logging in someplace else. In observe, most companies will persist with only a few choices, resembling these one-time passcodes despatched by way of textual content message to your cell quantity or generated in an authenticator app.
The issue with a second issue that depends on data out of your cellphone to authenticate logins is that if a malicious actor takes possession of your cellphone or can hack by means of and intercept information, your entry to your accounts can simply be compromised.
What’s a {hardware} safety key?
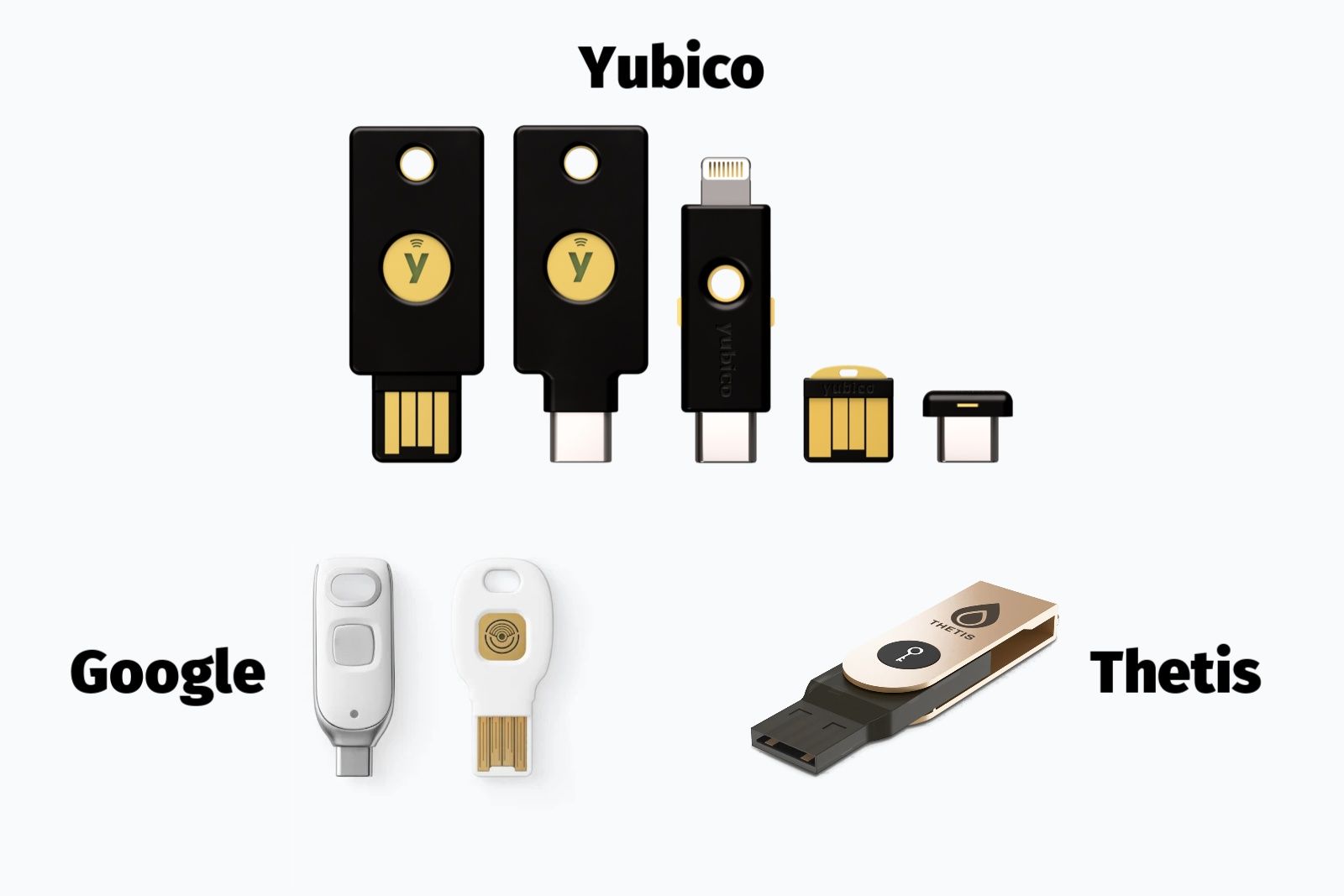
Google, Thetis, Yubico
That is the place {hardware} safety keys come into play.
Additionally identified merely as safety keys, common second issue (U2F) keys, or bodily safety keys, they take the second issue of authentication off your cellphone and make it a bodily (however tiny) dongle that plugs into the system of your alternative if you find yourself logging in – you will discover keys that join by way of USB-A, USB-C, Lightning, NFC, and Bluetooth. You’ll be able to hook them as much as a keychain or a darkish nook of your backpack and maintain them on you wherever you’re.
You’ll be able to successfully use a single {hardware} safety key for as many accounts as you wnat. Sometimes, you’ll both bodily insert or wirelessly pair the safety key to your required system after which press a button on the important thing itself when prompted throughout the login course of. Your net browser or app will then problem the safety key. It’ll cryptographically signal this problem, verifying your identification and no matter it’s you are making an attempt to entry.
Numerous producers make {hardware} safety keys and work with the most well-liked net browsers and a whole bunch of apps and on-line companies. They’ll even allow you to log into your workstation. Total, they are not onerous to make use of and are comparatively cheap. Just about some other type of two-factor authentication will not provide the identical stage of safety.
How do safety keys work?
The primary time you arrange a service together with your {hardware} safety key, the 2 sides will randomly generate a private and non-private key pair – the general public key will likely be despatched to a server, however the personal key won’t ever go away your {hardware} key. Your {hardware} key may also ship a random quantity referred to as a nonce, which is used to generate your keys, and one other quantity referred to as a checksum, which identifies your particular {hardware} safety key.
If you enter your login credentials into a web based account, the server will ship that nonce and checksum again to your {hardware} safety key and a distinct quantity. The {hardware} bodily key will use the nonce and checksum to regenerate its personal key after which signal the quantity despatched to it by the server, which finally verifies and unlocks your on-line account together with your public key.
The overarching requirements for a way safety keys retailer, current, and authenticate your credentials are decreed by the FIDO Alliance, a working group that features tech companies like Amazon, Apple, Google, and Microsoft, corporations that make password managers like 1Password and Dashlane, and even monetary establishments like Financial institution of America and PayPal.
All this sounds sophisticated. Nevertheless it occurs within the background with out your enter, aside from you inserting the {hardware} safety key into your system. {Hardware} safety keys additionally use the unique domains of web sites to generate their keys, which implies phishing websites cannot trick them.
We must also observe that the majority {hardware} keys may retailer and current static passwords and time-based one-time passcodes (like those from an authenticator app) for a restricted variety of companies. The primary commonplace you must look out for in relation to the meat and potatoes of a {hardware} secret is FIDO2.
The place can I exploit {hardware} safety keys?
You need to use {hardware} safety keys to log in to many desktop and cell units operating on ChromeOS, macOS, Home windows, Android, iOS, and different working methods. These similar units may also facilitate {hardware} key logins with supporting on-line companies and purposes, together with X (previously Twitter), Fb, Google, Instagram, Reddit, GitHub, Dropbox, Microsoft account companies, Nintendo, and others. Most net browsers like Google Chrome and Mozilla Firefox additionally assist {hardware} keys.
You must look into whether or not your most-used on-line accounts and even whether or not your units will assist safety keys earlier than you put money into one. The FIDO2 commonplace on some safety keys may work with Home windows Whats up and Microsoft’s Edge browser.
What if I lose my {hardware} safety key, or it will get stolen?
Your {hardware} safety key works along with your account login credentials. So, if somebody steals your key, they can not get into your accounts with out figuring out your username and password. Additionally, in case you’ve misplaced your safety key, you’ll be able to all the time resort to a backup methodology of two-factor authentication. You’ll be able to then achieve entry to your on-line account, take away your linked safety key, and both add one other or proceed utilizing a backup methodology.
arrange a safety key
As we have detailed above, all {hardware} safety keys are likely to work the identical, however setting them up varies by app and system. To present you an concept of how one works with a web based account, we have detailed the precise steps for pairing a safety key with Fb after which signing into your account:
- From both the app or web site, choose your profile image on the top-right nook of the display screen, then hit Settings and privateness, then Settings.
- You may see a panel referring to the Meta Accounts Heart. Choose See extra in Accounts heart
- Choose Password and safety, then Two-factor authentication.
- Choose the Fb account you wish to safe with a {hardware} key. It’s possible you’ll be requested to re-enter your password.
- You may then be supplied with an inventory of 2FA choices. Choose Safety keys after which hit Subsequent.
- Choose Register safety key. Your system’s working system will then ask you for the kind of safety key you are pairing with – NFC, Bluetooth, or USB. Affirm your key kind after which proceed to the subsequent immediate.
- Join your safety key to your system after which faucet the important thing’s button. You must obtain a affirmation message.
Which {hardware} safety secret is one of the best?
Yubico, which helps develop the FIDO U2F authentication commonplace, is without doubt one of the extra standard names within the discipline of {hardware} keys and has totally different fashions accessible. Google has its personal Titan key, which it refreshed in late 2023. Different safety key producers embody Kensington and Thetis.
We now have all of our particular picks for one of the best {hardware} safety keys in a devoted piece elsewhere on Pocket-lint.
Trending Merchandise

Cooler Master MasterBox Q300L Micro-ATX Tower with Magnetic Design Dust Filter, Transparent Acrylic Side Panel, Adjustable I/O & Fully Ventilated Airflow, Black (MCB-Q300L-KANN-S00)

ASUS TUF Gaming GT301 ZAKU II Edition ATX mid-Tower Compact case with Tempered Glass Side Panel, Honeycomb Front Panel, 120mm Aura Addressable RGB Fan, Headphone Hanger,360mm Radiator, Gundam Edition

ASUS TUF Gaming GT501 Mid-Tower Computer Case for up to EATX Motherboards with USB 3.0 Front Panel Cases GT501/GRY/WITH Handle

be quiet! Pure Base 500DX Black, Mid Tower ATX case, ARGB, 3 pre-installed Pure Wings 2, BGW37, tempered glass window

ASUS ROG Strix Helios GX601 White Edition RGB Mid-Tower Computer Case for ATX/EATX Motherboards with tempered glass, aluminum frame, GPU braces, 420mm radiator support and Aura Sync